Table of Contents
If an organization is subjected to the Health Insurance Portability and Accountability Act (HIPAA), its employees must understand the HIPAA compliance requirements for the privacy and security of Protected Health Information (PHI) are. HIPAA is a federal law that was established in 1996 outlining the use and disclosure of PHI. HIPAA compliance is enforced by the Office of Civil Rights (OCR) and is regulated by the U.S. Department of Health and Human Services (HHS).
Understanding HIPAA compliance requirements is incredibly essential. Failure to comply with HIPAA rules and regulations can result in considerable fines being issued, even if a PHI breach does not take place, while a PHI breach can lead to civil action lawsuits and criminal charges being filed. Organizations must also follow procedures with regards to reporting breaches of the HIPAA Privacy and Security Rules and issuing notifications to the patients as per the HIPAA Breach Notification Rule.
But what is HIPAA compliance? It involves fulfilling the requirements of the Health Insurance Portability and Accountability Act 1996, its succeeding amendments, and any related legislation, such as HITECH to protect the privacy, security, and integrity of PHI.
HIPAA Compliance Requirements – Who Must Comply?
Covered entities and business associates, as applicable, must comply with HIPAA Rules. If an entity does not meet the definition of a covered entity or a business associate, HIPAA Rules do not apply.
Covered Entities
By definition, any organization that collects, creates, or transmits PHI, is known as a covered entity. Healthcare organizations that are considered covered entities include:
- Covered healthcare providers such as chiropractors, clinics, dentists, doctors, nursing homes, pharmacies, and psychologists.
- Health plans such as health insurance companies, health maintenance organizations (HMOs), company health plans, and government programs that pay for healthcare (e.g Medicare and Medicaid).
- Health care clearinghouses such as billing services, repricing companies, community health management information systems, and value-added networks.
Business Associates
By definition business associates are organizations or people that encounter PHI in any way for the work that has been contracted to carry out tasks on behalf of a covered entity. Examples include:
- Billing
- Accreditation
- Consulting
- Data analysis
- Legal services
- Financial services
- Utilization review
- Management administration
What are the HIPAA Rules?

Before going into details about HIPAA compliance requirements, let’s review the HIPAA Rules. Employees must understand the rules first before an organization implements compliance requirements effectively.
HIPAA Privacy Rule
The HIPAA Privacy Rule only applies to covered entities such as health providers who conduct certain healthcare transactions electronically. It sets the national standard for the control of access to PHI, such as how PHI should be used and disclosed. The Privacy Rule gives patients the right to access their medical request information.
HIPAA Security Rule
The HIPAA Security Rule applies to both covered entities and business associates, especially when information is in transit between them. The HIPAA Security Rule sets the standard for security and coherence of the PHI, including handling of medical records whether they are physical or electronic. The main safeguards are within the security rule. This includes:
- Technical safeguards to protect electronic data such as data encryption.
- Administrative safeguards where policies and procedures on PHI protection are explained.
- Physical safeguards that involve actual physical structures such as controlling facility access or staff.
HIPAA Omnibus Rule
The HIPAA Omnibus Rule is an appendix that was added to HIPAA that made it mandatory for business associates to be HIPAA compliant, whereas previously, only covered entities were required to comply with it. This rule also sets the standard for Business Associate Agreements (BAAs). BAAs must be executed between organizations exchanging PHI before any information is exchanged.
HIPAA Breach Notification Rule
The HIPAA Breach Notification Rule sets the standard on how business associates and covered entities respond in case of a PHI breach. In case of a minor breach involving 500 or fewer people, the HHS breach must be notified of the breach within 60 days of the end of the calendar year. Larger breaches involving 500 or more people must be reported to the Secretary of the HHS within 60 days of discovery. In addition, affected victims must also be notified.
HIPAA Compliance Requirements
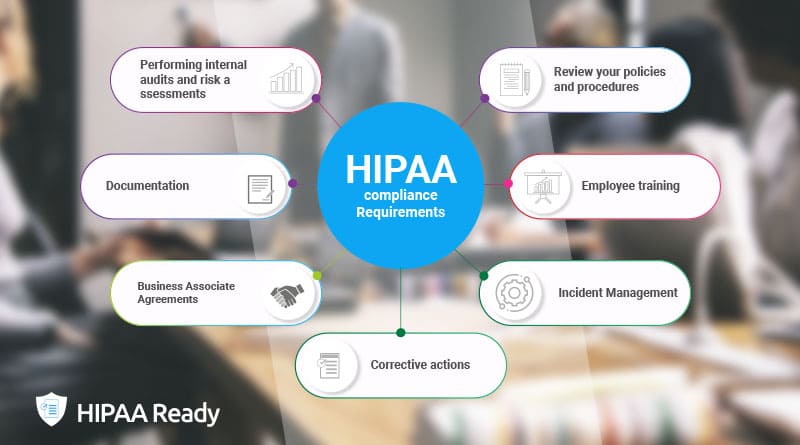
All covered entities and business associates must address the following guidelines to maintain an effective HIPAA compliance program:
Review your policies and procedures
Organizations must develop and implement policies that best reflect the regulatory standards as outlined in the HIPAA Rules. Policies and procedures must also be reviewed and regularly updated to account for the changes made by the OCR and ensure that the external stakeholders and patients are aware of these changes. To make things easier our robust cloud-based software, HIPAA Ready, allows users to easily update their policies and share across the organization.
Employee training
All employees are required to go through HIPAA training. Besides mandatory annual HIPAA training, conducting training regularly helps employees sharpen their understanding of the HIPAA law and lowers the risk of inadvertently violating the standards. With our software, authorized users can add HIPAA training courses, assign a trainee, and set a training schedule to make training management simpler.
Performing internal audits and risk assessments
Covered entities and business associates must conduct internal audits and risk assessments regularly to assess administrative, technical, and physical gaps with regards to HIPAA Privacy and Security standards. With HIPAAReady, organizations can perform these tasks regularly in a matter of a few clicks. The objective of this is to identify any potential threats to the integrity of PHI and resolve the issues as soon as possible.
Corrective actions
Once the threats and vulnerabilities have been identified after self-audits and risk assessments, covered entities and business associates must take corrective actions or make remedy plans to reverse compliance violations. These actions must be well-documented with corresponding dates, including dates on which the gaps will be corrected.
Business Associate Agreements
Covered entities and business associates must execute business associate agreements with all the vendors who may transmit, create, receive, or maintain PHI on their behalf. These agreements must be annually reviewed and updated to account for the changes to the nature of their practice or organizational relationships. Before any PHI is shared, BAAs must be executed.
Incident management
As per the HIPAA Breach Notification Rule, covered entities and business associates must have proper incident management procedures in case a PHI breach occurs. The breach must be documented and the patients must be notified about their PHI being compromised.
Documentation
The most important aspect of HIPAA compliance requirements is documentation. In a recent interview with a compliance officer of Utah Health Information Network (UHIN), she said the auditors collected around 127 documents, such as facility blueprints, organizational workflow charts, password policies, training logs, work desk procedures, and more. Easily maintain all the required documents using our software to reduce the hassle of finding these documents at the last minute before an official audit.
Manage HIPAA compliance requirements efficiently and effectively with HIPAA Ready
Based on years of experience in leading innovations, our legal advisers and experts have helped us build this robust HIPAA compliance software. It helps organizations to streamline their HIPAA compliance management processes by including a digital checklist of tasks, meetings, and training information. Leave a comment here to book a demo!
What is CloudApper AI Platform?
CloudApper AI is an advanced platform that enables organizations to integrate AI into their existing enterprise systems effortlessly, without the need for technical expertise, costly development, or upgrading the underlying infrastructure. By transforming legacy systems into AI-capable solutions, CloudApper allows companies to harness the power of Generative AI quickly and efficiently. This approach has been successfully implemented with leading systems like UKG, Workday, Oracle, Paradox, Amazon AWS Bedrock and can be applied across various industries, helping businesses enhance productivity, automate processes, and gain deeper insights without the usual complexities. With CloudApper AI, you can start experiencing the transformative benefits of AI today. Learn More